This week, the U.S. Cybersecurity and Infrastructure Security Agency warned consumers about “the worst cyber vulnerability in history.” This following the discovery of a technical flaw in the widely used Log4j software, used by millions around the globe that could “impact the entire internet,” according to CNN.
Cyber attacks on the rise
The news is the latest in a spree of cybersecurity hacks revealing vulnerabilities that potentially put your data at risk again. While Microsoft, Apple, Oracle and other big players are patching up holes and starting remediation. But, the exploits are just beginning. The incident is a reminder to more actively protect our cybersecurity with best practices – especially as we head into 2022, a year when cyber attacks are expected to rise:
“(2022) Attacks will range from extortions using stolen data to the penetration of critical supply chains. As well as looking for financial gain, the criminals will also increasingly use stolen data to discredit businesses and destroy reputations.”
Barracuda Networks
6 ways to boost your cybersecurity
1. Change your passwords – ALL of them
81% of breaches are caused by weak or reused passwords, it’s essential that each account have a unique password
-Last pass
This simple but effective action is worthwhile to revisit every year. Passwords to priority accounts like banking, brokerage, work and email accounts should be updated annually and ideally quarterly. According to SplashData, obvious and insecure passwords like ‘123456’ and ‘password’ are still popular making accounts easy to hack. Instead, create unique, complex passwords for every account. A tool, like Apple’s keychain, or other password management tools like LastPass, can help. They give sophisticated password suggestions, update them and remember them on any device.
2. Update your software
There’s often little we can do to protect ourselves when our accounts are exposed in a hack of big companies like Apple, Facebook and Google. In this case, the best (and only) defense is the updating of your software across all your devices, including your cellphones. Makers regularly update software to fix bugs and holes in their ecosystem that hackers have penetrated. Even with the automatic update setting enabled, you often have to “opt into” the updates by connecting your device to a power source or entering your passcode. It’s worthwhile to check your software is up-to-date monthly.
3. Update your internet browser settings (i.e. check your Google settings)
If you reflected on all the things you have searched for on your internet browser – you would know just how much revealing (and embarrassing) information your browser holds – your son’s odd-looking skin growth, birthday gifts for your mom and your whereabouts via maps. Google, for example, has key information from our using its browser, email, calendar products and even its phones. This allows the company to send you targeted ads, which makes the company money. This is why the Nordstrom sweater you were ogling shows up as a pop-up ad for the next week. Limit the way Google and other browsers, like Safari and Bing, use your information.
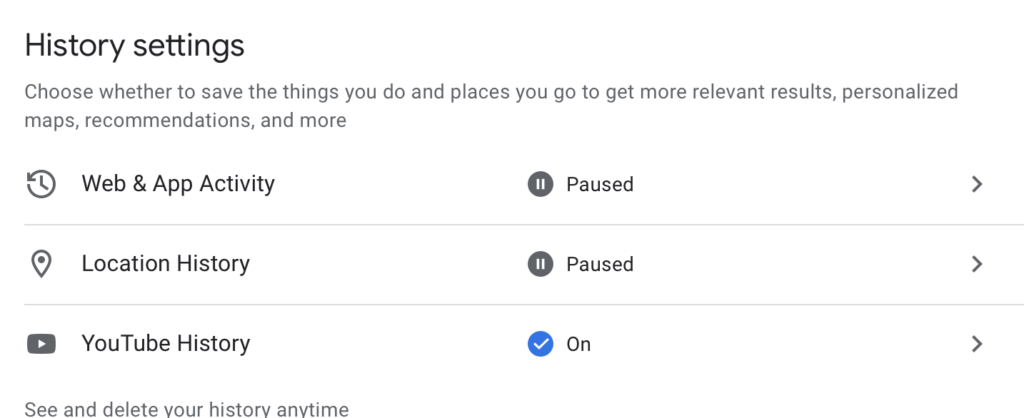
Start by reviewing the privacy settings in your Google Account and using tools like Dashboard and My Activity, which give you transparency over data collected from your activity across Google services.
On the Web, go to myaccount.google.com → Data & Privacy → Web & App Activity. Turn off the toggle for Web & App Activity so it is gray instead of blue. This is the most impactful setting “that does the most to stop Google from tracking your search and browsing activity,” according to the Washington Post.
4. Consider an alternative internet browser and email provider
Switching to sites like Duck Duck Go can also offer a more private browsing experience. Proton mail is an encrypted email service offering more secure email.
5. Set up 2-factor authentication
This extra step is significant in safeguarding your account in conjunction with a sophisticated password. This feature is especially recommended for finance-related sites (banking, Paypal, retirement accounts, etc.) Two factor authentication adds an extra security layer to the standard method of logging on with your password. It simply sends a code to your phone or email to verify your identify before letting you log in. In the event your account is hacked or your device stolen, this additional measure better protects your accounts.
6. Don’t forget to review your social media settings
As recent headlines show, our data is vulnerable even on social media sites. As we are learning, more friends isn’t always better. Our profiles can be used to phish for information, deliver spyware and even be surveyed by government entities. In general, don’t friend people you don’t know well. Be sure to check privacy settings across all your platforms, including professional ones like Twitter and LinkedIn. Always think before you post. The following are specific tips for various social media platforms, as suggested by the University of Cincinnati and Internet Matters, which provide comprehensive support and resources:
- Facebook: While it is fun to share your high school, birthday, and even your hometown with your friends, it is considered personally identifying information (PII). Paired with other information, these facts could potentially be used to compromise your bank accounts or even your identity.
- LinkedIn: While oversharing your career history could lead to tax fraud or social engineering, undersharing your job skills could affect your networking opportunities. Choose carefully which details you want to share with the world.
- Instagram: To keep your photos private, tap “Edit Your Profile” next to your profile picture and turn on the “Posts are Private” setting. Be sure to save your changes. Please remember that regardless of your privacy settings, any user will still be able to read your bio, and send a photo or video to you directly.
- TikTok: Family Pairing allows parents and teens to customize their safety settings based on their needs. Turning on Screen Time means you can set your child’s watch time by using a passcode. The Restricted Mode feature can help limit the appearance of content that may not be suitable for children. Please note that even with a private account your child’s profile photo, username, and bio will be visible to all TikTok users. It is best to ensure no sensitive or personal information is included here. If you select Filter all comments, all comments will be hidden unless you approve them.