News of Bose Headphones sharing private user information drove me into stealth mode to discover other tech devices exposing you to vulnerabilities. Be careful what you say in front of your TV!

You pay a fortune for high quality headphones, TVs and even cars, and then they go behind your back and spy on you. Last week, A lawsuit was filed against pricey headset maker, Bose. A customer accusing it of misrepresenting the need to download the Bose Connect app. The company touted the app was necessary to “get the most of your headphones,” but the app recommendation appears purely aimed at collecting valuable usage stats. The company was possibly selling customer data to third parties. Tucked into Bose’s fine print are clauses that allows the firm to sell that information to third parties. However, the language was not presented to customers first. According to Fox Business, “customers do not see the Bose app’s user service and privacy agreements when signing up, and the privacy agreement says nothing about data collection.”
So, how can we increasingly protect ourselves from the multiplying number of IoT, connected devices that pile up in our home, office and car? Here are some common devices you likely have, which could pose a sharing or security threat, and how you can easily defend against security shortfalls.
1. The snooping capability of your Smart TV

Despite their name, SmartTVs are anything but smart, except for their snooping capabilities. As you lounge in your living room, your TV set could be recording your couch commentary and watching you through its camera. Even the government knows smart TVs are the easy way to spy! Despite their connected capabilities, Smart TVs don’t posses the same security support features that your phone, tablet and other devices may have. Not only do most TVs relay your personal viewing habits to the manufacturer as a standard practice. Many major brands, including Samsung and Vizio, have been involved in security incidences and caught selling your personal data to third parties.
[information]Tip 1: Ensure your TV runs the latest software
Tip 2: Split your WiFi signal, using it just for the TV. Disconnect from WiFi when not in use
Tip 3: Turn off the smart features of your TV[/information]
2. The eavesdropping features of your Amazon Alexa and Google Home devices

Yes, these at-home personal voice assistants have become irreplaceable for instant weather and traffic updates, even entertaining your kids, as I covered last month. As the devices wait for your beckoning call, they remain passively present in the background, waiting for you to wake them up with a call of “Alexa” or “Google.” This means they are just “listening” in the background. Both companies insist they take tough security stances with the audio data collected and requests. They insist the devices don’t begin recording until the “wake” word is uttered. Recordings are encrypted and the hardware is secure, perceived secure against hackers (for now).
[information]Tip 1: Mute your device when not in use. Press the mute button on the device to do this
Tip 2: Request your device play a sound at the start and end of a request (Alexa app only)
Tip 3: Delete archived audio recordings (Alexa app only)[/information]
3. The spying eyes of your laptop computer
Did you know your computer’s webcam and microphone are common targets for hackers, for their abilities to intercept your most private moments? Well, Mark Zuckerberg knows it.
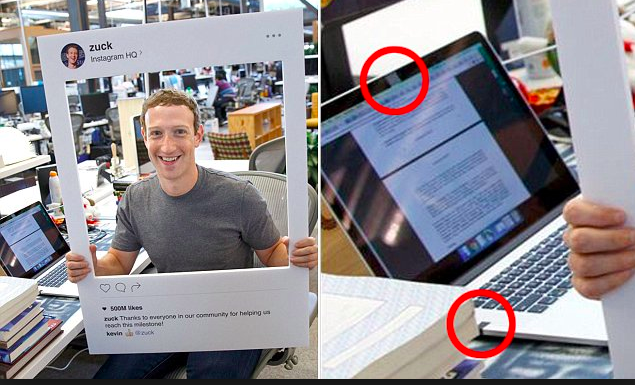
In this photo that made the rounds last summer, a Twitter user noticed how the Facebook exec chose rudimentary methods to secure his laptop camera and microphone jack: with black electrical tape. The reason? Covering your two way video and audio outputs is a basic measure in laptop (or desktop) security. In fact, according to the New York times, “covering the camera is a very common security measure (in the tech industry).” Software security firm, Norton, also suggests keeping an eye on the indicator light on your laptop, if you have one. If it starts coming on for no reason, that’s a good sign that your system has been compromised.
[information]Tip 1: Make sure you update your device’s software and have malware detection Tip 2: Cover your device’s video camera and microphone with tape [/information]
4. Hands-free driving, courtesy of hackers
As self driving cars become more popular, they draw the attention of hackers and malware attacks. It isn’t just the fancy Teslas that are vulnerable, even standard vehicles are, as well. Two years ago, Chrysler had to recall 1.4 million vehicles after hackers showed they could remotely take control of a Jeep using a simple laptop and the internet to control its software.
Chinese firm, Tencent, made news when it showed how it could break into a Tesla’s computer system to operate the vehicle’s breaks. Tesla and other vehicle makers work continuously to patch up security holes and issue immediate security updates, but the ongoing risk exists. With the increase in IoT features in cars of all types, breaches are sure to follow.
[information]Tip 1: Upgrade car software regularly
Tip 2: Go to reputable dealers and repair shops to minimize chance of foul play
Tip 3: Create car-specific passwords[/information]